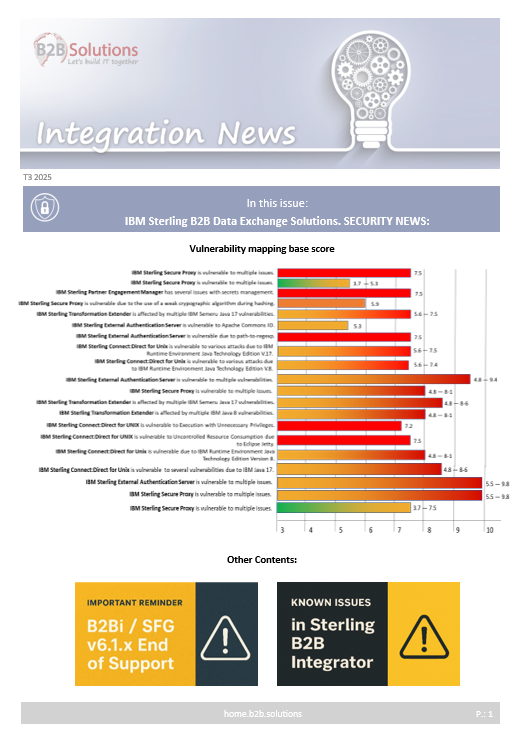
IBM Sterling External Authentication Server is vuulnerable due to path-to-regexp
Summary
IBM Sterling External Authentication Server uses the npm path-to-regexp, which is vulnerable to CVE-2024-45296.
Vulnerability Details
CVEID: CVE-2024-45296
Description: path-to-regexp turns path strings into a regular expressions. In certain cases, path-to-regexp will output a regular expression that can be exploited to cause poor performance. Because JavaScript is single threaded and regex matching runs on the main thread, poor performance will block the event loop and lead to a DoS. The bad regular expression is generated any time you have two parameters within a single segment, separated by something that is not a period (.). For users of 0.1, upgrade to 0.1.10. All other users should upgrade to 8.0.0.
CWE: CWE-1333: Inefficient Regular Expression Complexity
CVSS Source: CVE.org
CVSS Base score: 7.5
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H)
Affected Products and Versions