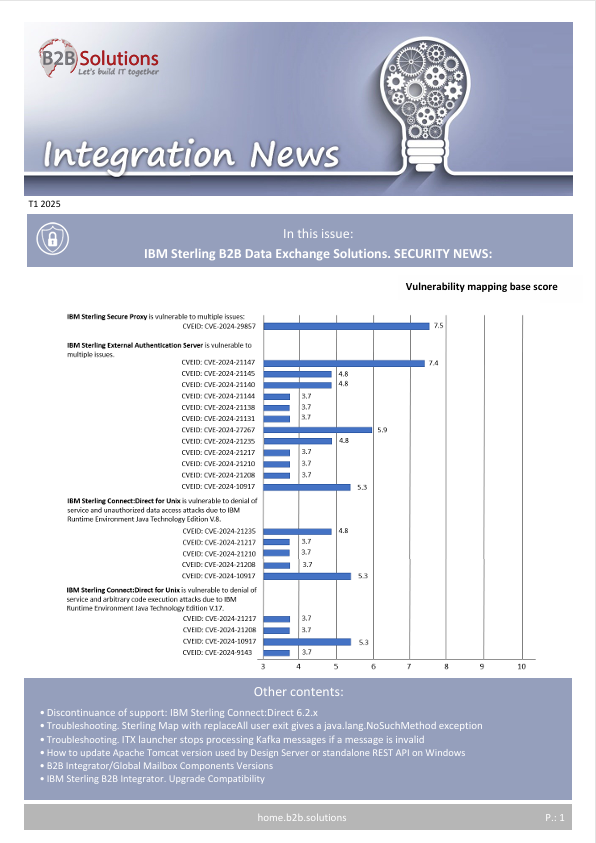
IBM Sterling Connect:Direct for Unix is vulnerable to denial of service and attacks due to IBM Runtime Environment Java Technology Edition V.17.
Vulnerability Details
CVEID: CVE-2024-21217
Description:Vulnerability in Java SE (component: Serialization). Difficult to exploit vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS).
CVSS Source: Oracle
CVSS Base score: 3,7
CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L)
CVEID: CVE-2024-21208
Description: Vulnerability in Java SE (component: Networking). Difficult to exploit vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Java SE. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS).
CVSS Source: Oracle
CVSS Base score: 3,7
CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L)
CVEID: CVE-2024-10917
Description: In Eclipse OpenJ9 versions up to 0.47, the JNI function GetStringUTFLength may return an incorrect value which has wrapped around. From 0.48 the value is correct but may be truncated to include a smaller number of characters.
CVSS Source: NVD
CVSS Base score: 5,3
CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N)
CVEID: CVE-2024-9143
Description: OpenSSL could allow a remote attacker to execute arbitrary code on the system, caused by an out-of-bounds memory read or write flaw due to the use of the low-level GF(2^m) elliptic curve APIs with untrusted explicit values for the field polynomial. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code or cause the application to crash.
CVSS Source: IBM X-Force.
CVSS Base score: 3,7
CVSS Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:L)
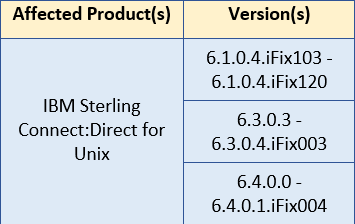
Affected Products and Versions