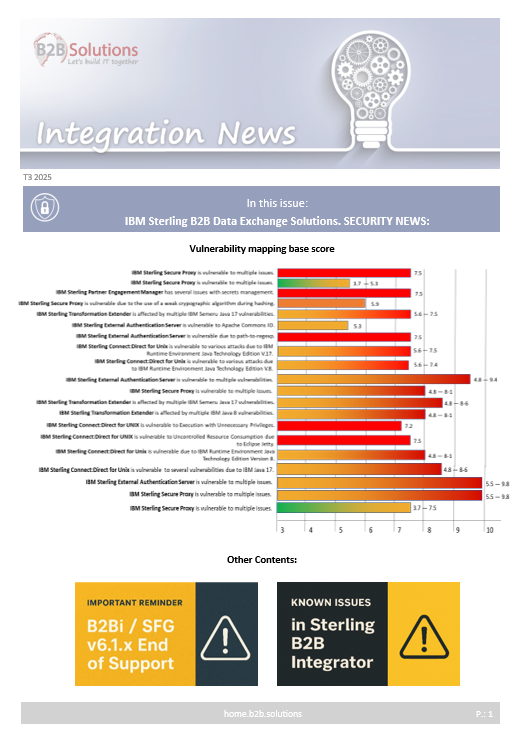
IBM Sterling Connect:Direct for UNIX is vulnerable to Execution with Unnecessary Privileges.
Summary
IBM Sterling Control Center can apply maintenance to and upgrade IBM Sterling Connect:Direct for UNIX. The Control Center administrator has the option of running pre and post update scripts. Those scripts are run as root; they should be run as the standard user account under which Connect:Direct UNIX was installed.
CVEID: CVE-2025-36137
Description: IBM Sterling Connect:Direct for UNIX incorrectly assigns permissions for maintenance tasks to Control Center Director (CCD) users that could allow a privileged user to escalate their privileges further due to unnecessary privilege assignment for post update scripts.
CWE: CWE-250: Execution with Unnecessary Privileges
CVSS Source: IBM
CVSS Base score: 7.2
CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
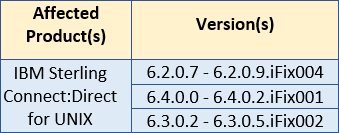
Affected Products and Versions